Cybersecurity: Governance & strategic risk management

“Cybersecurity needs to be approached through a strategic risk management process with the identification and prioritisation of known threats and vulnerabilities.”
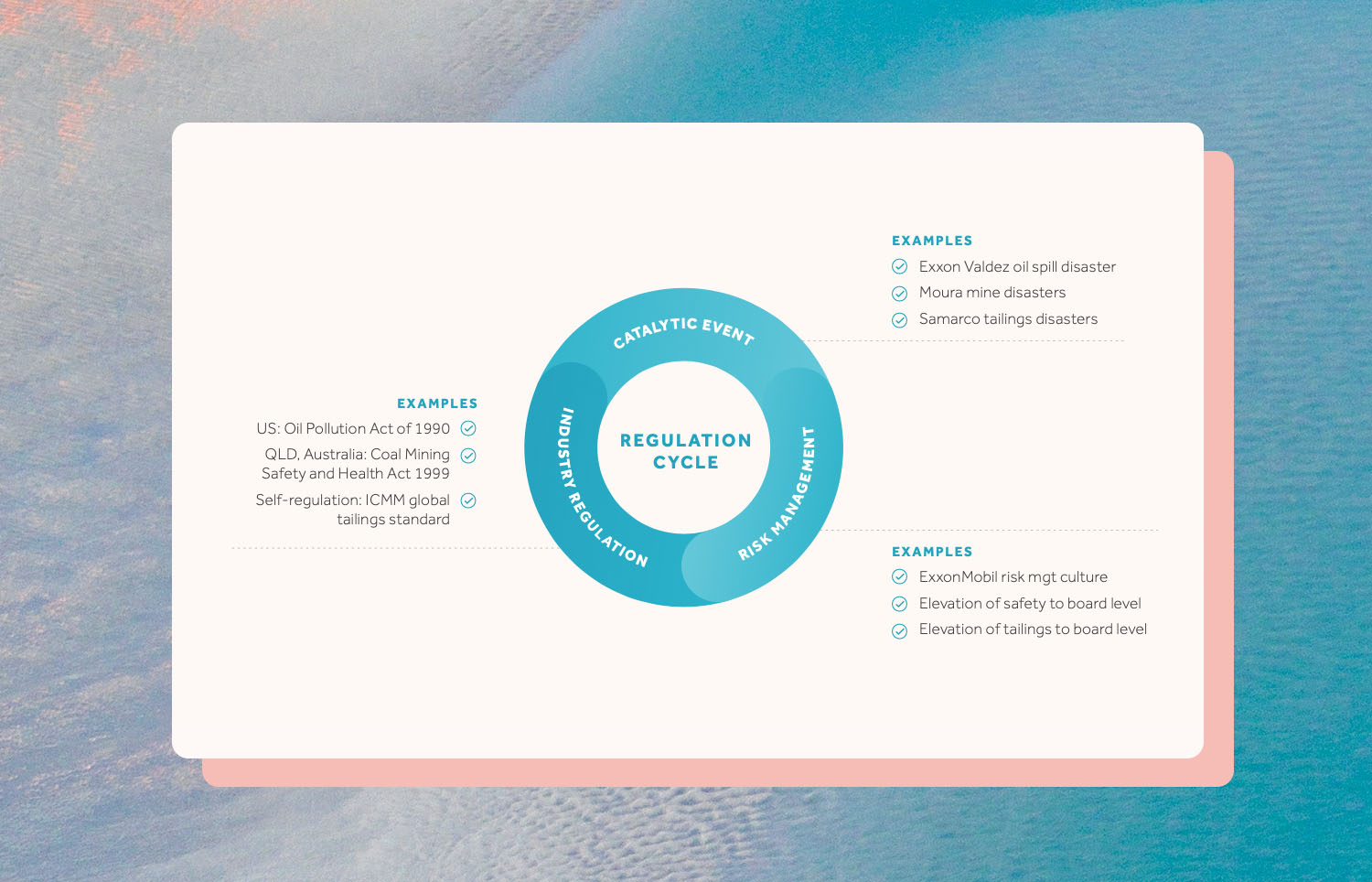
Perhaps surprisingly, the interviews revealed that chief information security officer roles focus more on people and processes than on the technical aspects of cybersecurity. Risk management is being applied as the vehicle for managing cybersecurity across these large, well-run natural resource businesses. It is considered highly useful because of the complex and dynamic nature of the cyber challenge combined with the natural affinity and competence with it as a methodology. Cybersecurity lends itself to a risk-based prioritisation and mitigation process, in the same way that other strategic risk areas are managed such as safety, environment and market risks. As a high-risk endeavour with a highly risk conscious temperament, mining’s capability and culture is extremely well adapted to managing issues in this way.
Cybersecurity is different from other strategic risks in one important dimension – adversaries are dynamic and incentivised to adapt. Adaptation at this rate is not the case for other major risks like safety and environmental risks. As such, and despite the good initial fit, risk management methodologies can’t be adopted for cybersecurity without adaptation. Attackers can ‘change the incentives, and hence behaviours, of the defenders.’ The reverse is also true. This kind of thinking ‘opens up novel mitigation strategies beyond the traditional risk management thinking.’ A salient example of this is the effectiveness of an entire industry banding together to refuse to pay ransoms from ransomware, thus ‘reducing the incentives of the attackers to attack in the first place.’
Technology may come to be a key tool for risk management more broadly, the ability to apply analytics for soft sensing and detection of issues or to virtually simulate operational scenarios (to pre-empt occurrences) is accelerating quickly. Strategic risks, such as cybersecurity, have always posed a general challenge of low probability, high consequence events – lending itself to the application of such simulation principles.
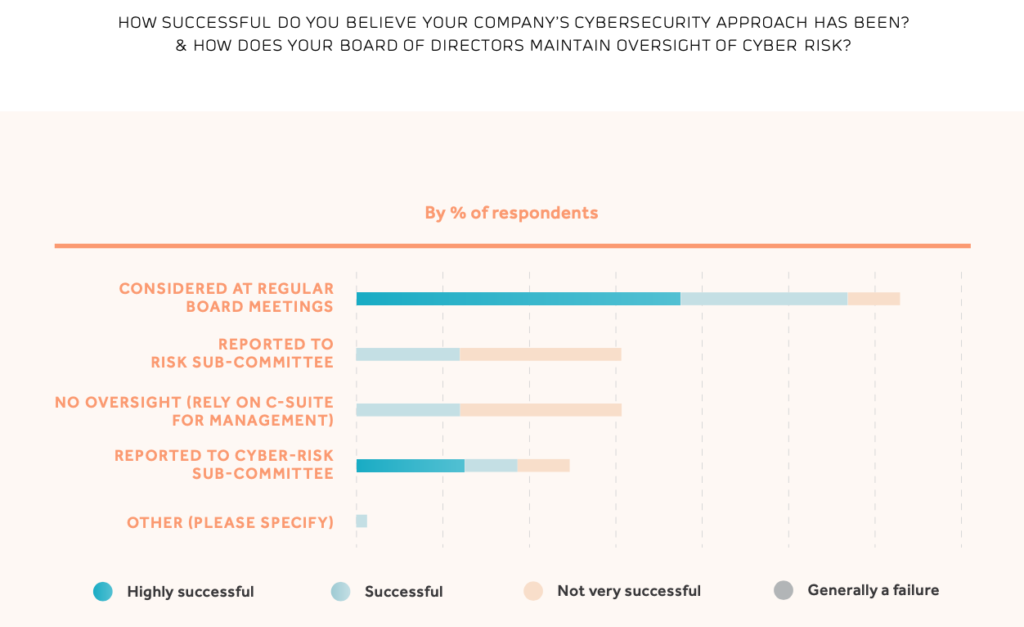
Cybersecurity has quickly vaulted up most lists of global or business strategic risks to the point that around three quarters of all mining companies provide some level of oversight of cyber risks at the board level. This is sensible and desirable as boards form a crucial piece of the puzzle in forming a response to cyber risks – notably, among all respondents, board members are most aware of cybersecurity issues. Despite this awareness and prioritisation, ‘boards today are poorly equipped to meet cybersecurity challenges; they do not have the experience or worldview necessary as problems in this era become increasingly digital.’
“Boards need to understand the implications of cybersecurity in the language of finance, reputation, competitive position and customer trust. They do not need technical knowledge as it changes too fast to be useful to them.”
Boards must be able to filter technical advice from their security executives in order to make judgements on strategic implications and prioritisation. This is the perennial issue for all strategic risks; they are always technically complex. Mining boards have been chastened by recent events such as tailings dam failures, environmental impacts, exposure to terrorism and geopolitical volatility among major trading partners – getting strategic risk management methodologies in place is at the top of their agenda. They see deficiencies in approaches to strategic risk management across the board and are searching for mechanisms to improve.